Whaling attacks are a sophisticated form of cyber-attack aimed at high-profile individuals within organizations, such as executives, CEOs, and senior officials.
These attacks are a more advanced version of phishing, dubbed “whaling” because the targets are the “big fish.” The primary objectives of these schemes include stealing sensitive information, gaining unauthorized system access, or coercing the target into approving financial transactions
Table of Contents
Characteristics of Whaling Schemes:
1. Highly Targeted: Unlike generic phishing, whaling schemes are customized for the individual target. Attackers conduct extensive research, often utilizing publicly available information from social media, company websites, and other sources.
2. Spoofed Emails: Attackers frequently use email addresses that seem to originate from trusted sources, such as colleagues, business partners, or reputable organizations. They may also employ domain names that closely resemble legitimate ones.

3. Urgency and Authority: The communications often create a sense of urgency or leverage the authority of the sender to compel immediate action. For instance, an email might assert that prompt payment is necessary to avoid legal repercussions or that sensitive information needs urgent verification.
4. Requests for Sensitive Information or Actions: These emails may solicit sensitive details like login credentials, financial data, or personal information. Alternatively, they might urge the target to authorize large financial transactions or alter vendor payment details.
5. Social Engineering: Whaling attacks heavily rely on social engineering tactics to manipulate targets into compliance. This can involve building trust over time or exploiting personal relationships. Some attackers may attempt to engage their targets at major events, initiating friendly conversations or presenting themselves as highly successful.
Examples of Whaling Schemes
- CEO Fraud: An attacker impersonates the CEO or another senior executive, sending an email to a finance department employee, instructing them to transfer funds to a designated account.
- Legal Subpoena: The target receives an email that appears to be from a legal authority, demanding sensitive information with threats of legal consequences.
- Vendor Email Compromise: An attacker poses as a trusted vendor, requesting a change in payment details to redirect funds to their account.
Prevention and Mitigation:
1. Employee Training: Conduct regular training sessions to educate staff about the dangers of whaling and how to identify suspicious emails.
2. Verification Procedures: Implement stringent verification protocols for any requests involving sensitive information or financial transactions, such as multi-factor authentication or verbal confirmations.
3. Email Filtering: Utilize advanced email filtering solutions to identify and block spoofed emails or those containing malicious links.
4. Incident Response Plan: Develop and maintain a response plan to swiftly address any suspected whaling attacks.
5. Regular Audits: Perform regular audits of financial transactions and account changes to detect unauthorized activities.
By comprehending the nature of whaling schemes and employing robust security measures, organizations can significantly mitigate the risk of falling prey to these targeted attacks.
In the next edition, we will discuss ATM card fraud and strategies for prevention.
About the Author
Charles Akinjide Ogunmoriyele is a chemical engineering graduate of Obafemi Awolowo University, Nigeria. He founded Edward Louis Limited, focused on renewable energy, real estate, manufacturing, and cybersecurity. Motivated by a personal incident involving cybercrime in 2018, he pursued cybersecurity education and certifications and now an advocate of cyber security awareness. He can be reached via email at edwardlouislimited60@gmail.com
See also:
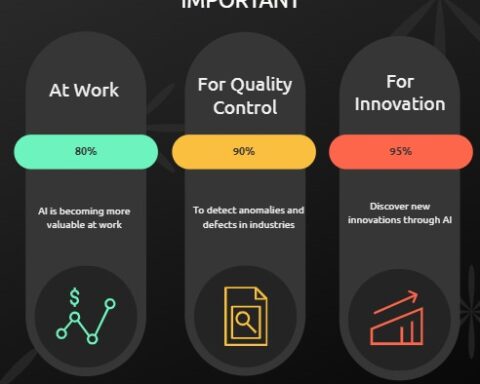
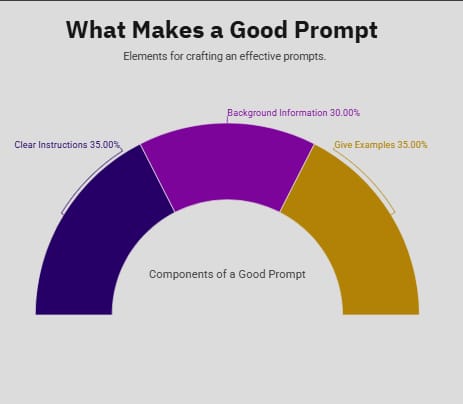
What is prompt engineering and why is it important?
The Imperative of Cybersecurity Awareness
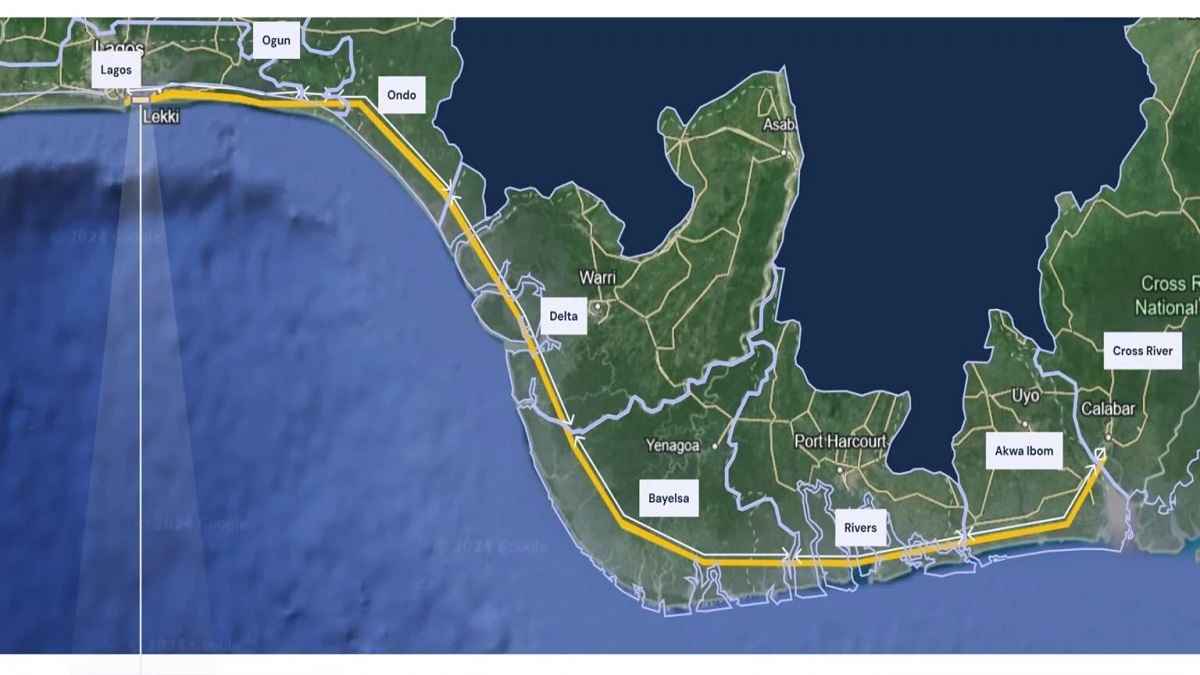
Lagos–Calabar Coastal Highway: The significance of Celebrating 30km out of 700km. By Yomi Akinfesoye






System audit is also a way of identifying attackers within the organisation.
Well researched .Thank you
The CEO fraud almost happened in an organisation I worked for in the past, but thank God for my penchant for details and sticking to processes and procedures.
It wasn’t funny at all and it almost led to the firing of a GM and the Head of Operations who unknowingly pressured me into making an urgent payment into a fraudulent account!
At my first glance at the email, I discovered what the GM and the Head of Operations (who were in copy of the fraudulent email) couldn’t see – replacement of Letter O with number 0.
Companies must teach their staff to be more observant and to respect processes and procedures. They help.